When dealing with digital security, it is good not to rely only on the protection of end devices in the form of a popular antivirus platform.
Especially in the case of servers and company applications, it is necessary to look at their security from multiple sides and in multiple layers. And this is where the Wazuh platform comes in, which helps to gain an overall overview and control over the security status of the IT infrastructure.
The whole solution, also referred to as SIEM, consists of a single universal agent, installed on the monitored device, and three central components: the Wazuh server, the Wazuh indexer and the Wazuh control panel.
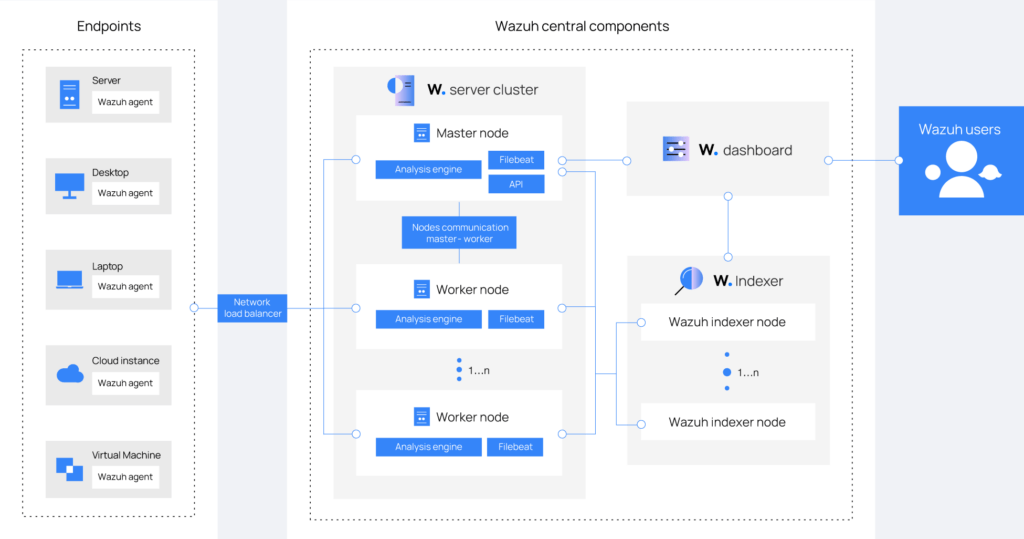
Why did we choose Wazuh as a SIEM?
There are many platforms for security monitoring, especially commercial ones. Wazuh impressed us primarily with its abilities, approach and openness.
Wazuh uses multiple different sources of threat information to improve its detection capabilities. It enriches the obtained data using the MITRE ATT&CK framework and compliance and regulatory requirements such as PCI DSS, GDPR, HIPAA, CIS and NIST 800-53, thus providing a useful context for obtaining an overall overview and control over actions and state of the IT infrastructure.
How Wazuh can help you with security
Log analysis and archiving
In many cases, evidence of suspicious activity can be found in a log file of monitored system or application. Wazuh will help with the automation of log management and analysis and thus can speed up the detection of both external and internal threats.
Thanks to the powerful indexer, it also helps with the preservation of logs for further forensic analysis as well as to fulfill regulatory and internal retention requirements.
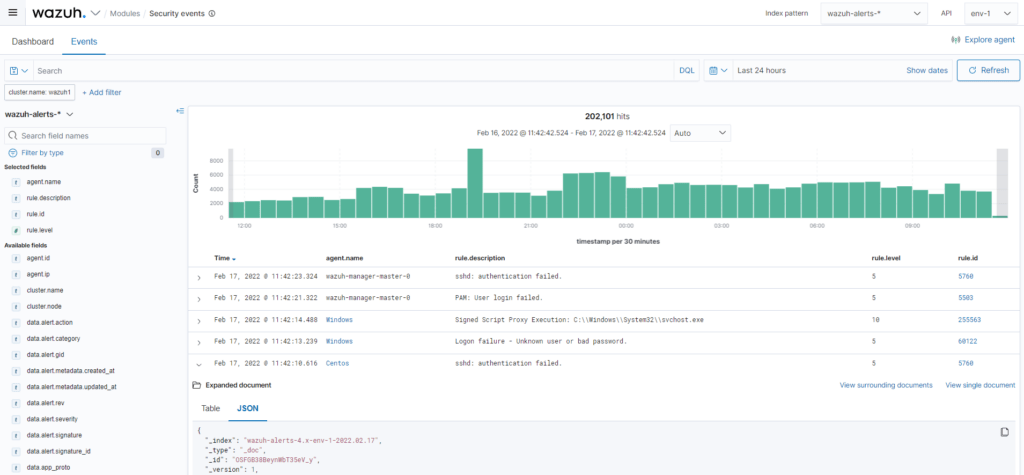
System inventory
The inventory module collects hardware and software information from the monitored system. This tool helps to identify assets and evaluate the effectiveness of patch management.
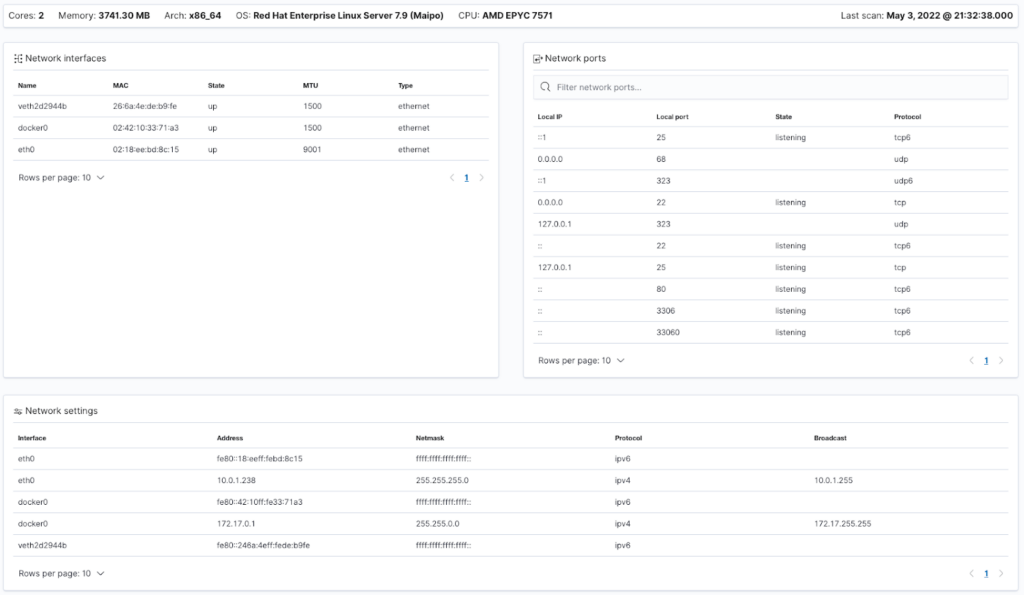
The collected inventory data for each of the monitored devices can be searched through the Wazuh RESTful API and from the web user interface. These include memory usage, disk space usage, processor specifications, network interfaces, open ports, running processes and a list of installed applications.
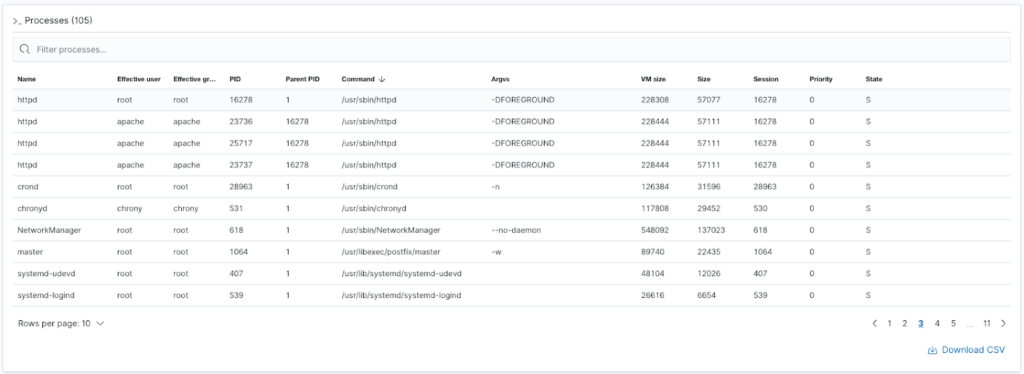
Collection of inventory data is performed automatically and regularly according to the settings. After the collection is complete, the new inventory data is compared with the old data from the previous scan. In this way, it identifies (for example) the opening of a new port, changes in processes or the installation of a new application.
Monitoring the compliance with regulatory requirements – CIS, PCI DSS etc.
Are your GPOs compliant with security recommendations? Is your AD secured according to the CIS specification? The Automated Configuration Assessment module helps maintain a standard configuration by monitoring the configuration of monitored devices.
The module regularly scans and reports incorrect configurations in the monitored system. These scans assess the system configuration through policy files containing a set of checks. For example, it can check the file system configuration, look for the availability of an update or security patch. It can also check whether a firewall is enabled, identify unnecessary running services, or verify user password policies.
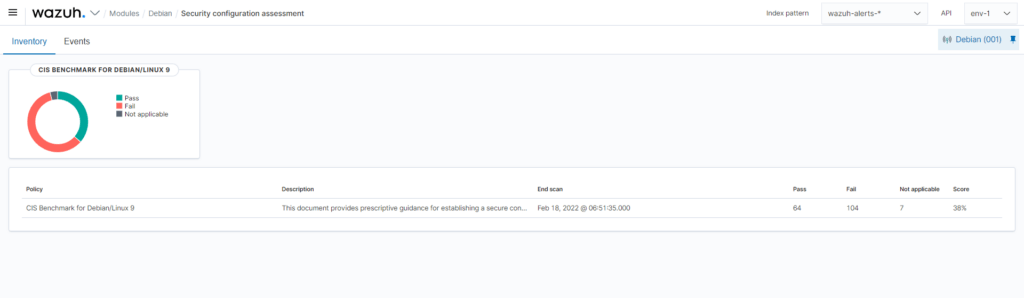
Scanning policies are written in YAML format. This allows users to quickly understand them, as well as extend existing policies to suit their needs or to write new ones.
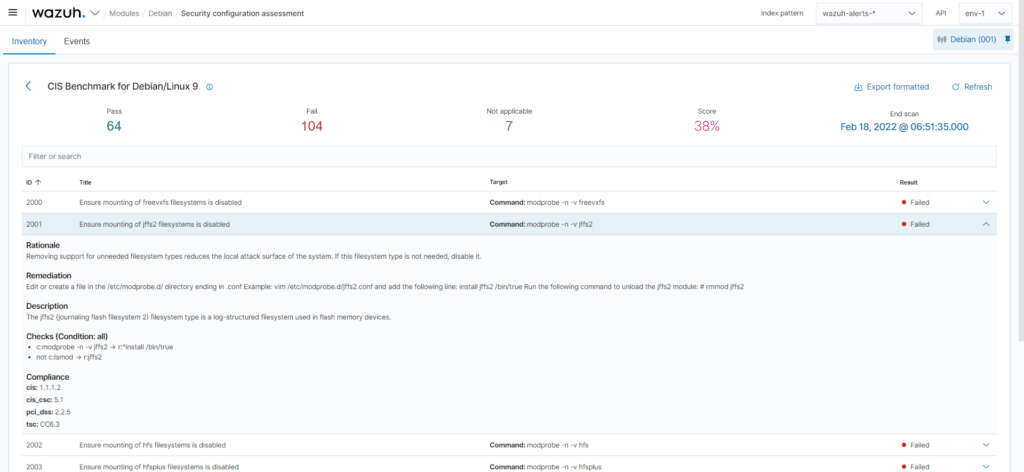
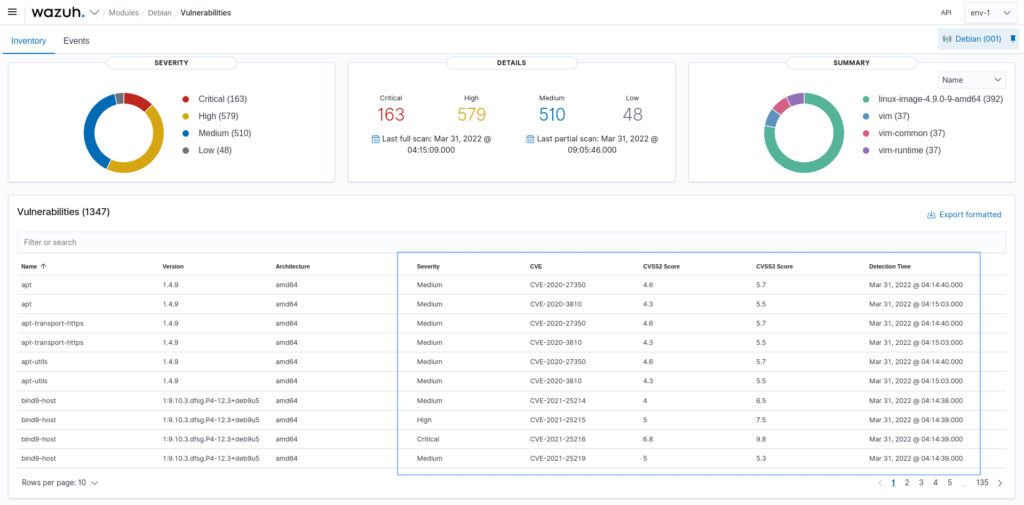
Vulnerability detection
Wazuh can perform regular, automatic vulnerability detection. It helps to detect vulnerabilities in operating systems and applications installed on monitored devices in a timely manner.
The vulnerability detection module is integrated with external vulnerability information sources. These sources are for example Canonical, Debian, Red Hat, Arch Linux, Amazon Linux Advisories Security (ALAS), Microsoft, and the National Vulnerability Database (NVD).
Wazuh maintains a list of applications installed on monitored devices and regularly compares it with a database of vulnerabilities (CVEs). The output is an overview of vulnerabilities, including additional information and recommendations.
Members of the security team thus obtain an up-to-date overview of the state of vulnerabilities and can react effectively and in a timely manner.
Active protection
A very useful part of the Wazuh platform is the active protection module. This module makes it possible to automate reactions to events in monitored systems. Automation ensures timely and consistent resolution of selected incidents, which can be especially valuable for smaller teams with limited resources.
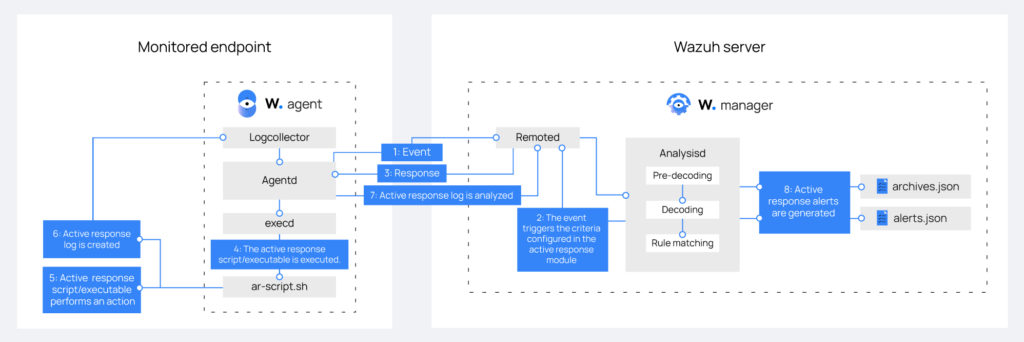
The module contains a number of response scripts to help respond to and mitigate threats. For example, the scripts block malicious network access or delete malicious files on monitored devices. Automatic actions thus reduce the workload of security teams and enable them to manage incidents efficiently.
Integrity checks
The integrity check module regularly monitors the system and stores checksums, attributes and other properties of files and/or registry keys. By comparing the obtained information, it detects changes made on the monitored system and sends them to the Wazuh manager. An alert is generated whenever changes are detected in monitored files and/or registry keys.
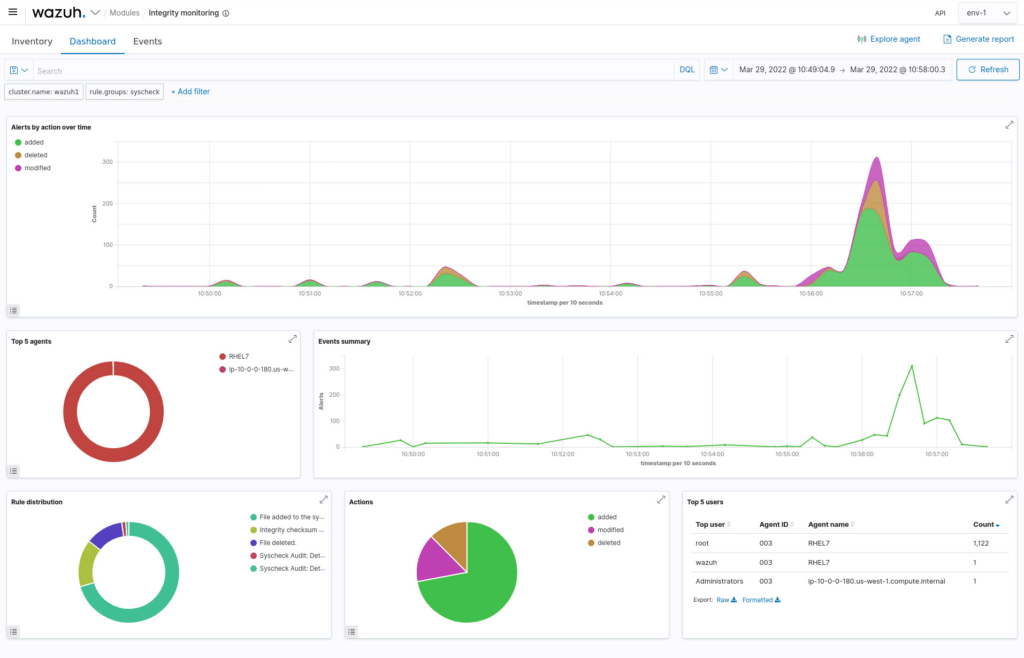
Cloud security
Wazuh also allows you to monitor your service infrastructure in popular cloud service providers. These include Microsoft Azure, Amazon AWS or Google Cloud, as well as in Office 365.
Through the previously mentioned components, you can monitor servers operating in a cloud. Thanks to integrations with APIs of cloud service providers, it can also monitor activities related to the management of cloud environments and activities performed by users.
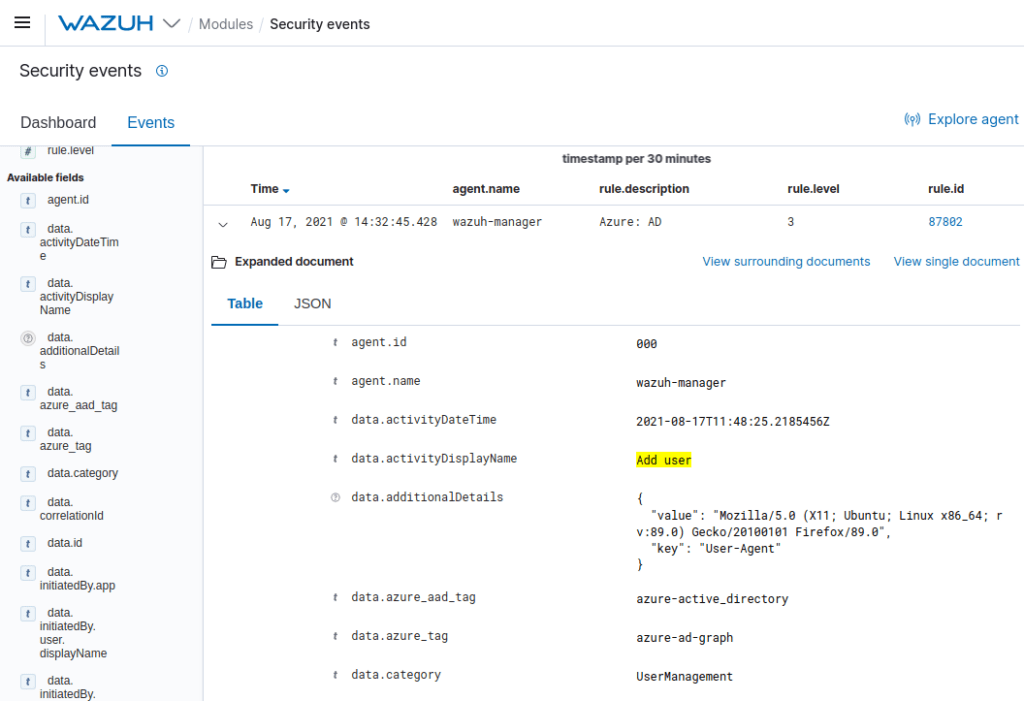
For example, the Azure Logs component allows you to monitor all activity and services of your infrastructure in Microsoft Azure. Such as activity logs, resource logs or Azure Active Directory logs.
Container security
The Docker platform is also an integral part of many corporate environments. Here too, Wazuh can provide you with the necessary overview. It monitors container behavior and can thus detect possible threats, vulnerabilities and anomalies.
Thanks to its native integration with the Docker environment, Wazuh allows users to monitor images, volumes, network settings or running containers.
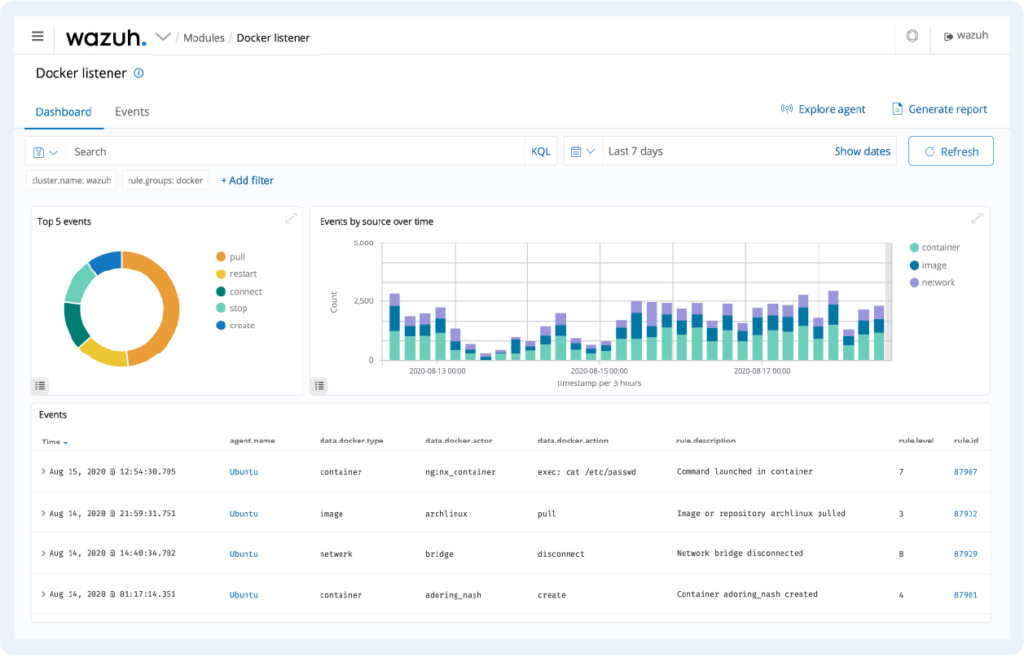
Wazuh continuously collects and analyzes detailed information about the running of containers. For example, it warns about containers running in privileged mode, vulnerable applications, a shell running in a container, changes to persistent volumes or images, and other possible threats.
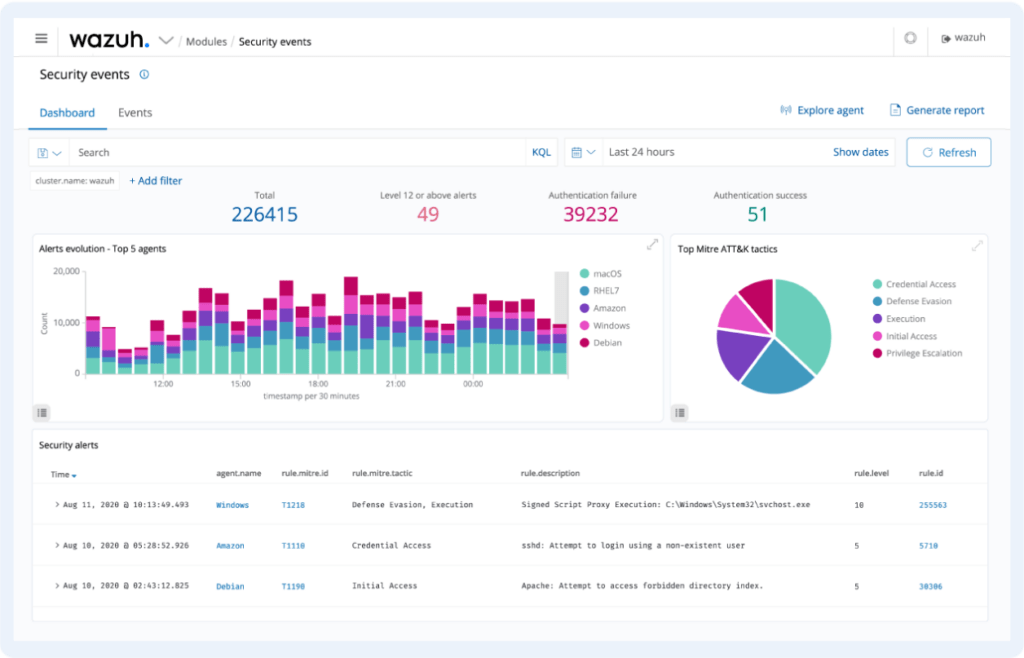
Custom dashboards, reporting and alerting
Thanks to the wide options for overview panels settings, reporting and alerting, not only the IT administration, but also the risk management and security team can easily and quickly get an overview of (for example) suspicious activities, changes to AD, firewall rules or user permission settings on monitored systems.
Are you interested in the SIEM capabilities of the Wazuh platform?
You can learn more about the open-source security capabilities of the Wazuh platform in our webinars:





Give us a Like, share us, or follow us 😍
So you don’t miss anything: