Identity Management
Employees come, employees go, and everyone needs to be taken care of. They need not only their workplace, but also the right access to all the necessary information systems (IS). But if they leave the company, this access must be taken away. That’s what identity management is for. It’s the foundation of problem prevention and IT security for small, medium and large companies.
IDM is a fast, accessible, flexible and affordable solution

IDM securely and efficiently manages assigned permissions

It provides a central overview and access management as well as reports for auditing purposes
Why deal with Identity Management
Almost every company today is using more and more systems, applications and technology platforms to improve work efficiency and collaboration among employees and suppliers. This presents a multitude of accesses and the need to store passwords. This is where security risks arise – losing passwords, sharing passwords among multiple people, access by unauthorized personnel or even former colleagues or contractors.
Different systems require different rules and requirements, which creates room for the risk of human error. At the same time, your colleagues want to keep all access and its management as simple and fast as possible. On top of that, there are requirements in the area of increased security, often with the threat of fines with regard to contractual terms with customers, then the Cybersecurity Act, GDPR, etc.
We must also not forget that most cyberattacks today are directed through leaked identities and access. This also shows that the topic of identity management is important and should not be underestimated, especially nowadays.
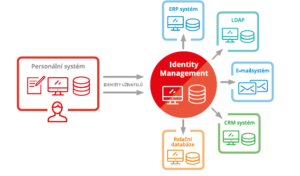
Benefits of IDM for companies
Creating processes and setting up identity management systems correctly brings a number of benefits:
- Centralizing identity management in one place for all types of accounts
- Increased clarity of identity management
- Ensuring consistent identity across technologies and systems
- Reducing the time required to control and manage identities
- Unifying user rights and roles
- Security and risk minimisation (especially for sensitive data leakage)
- Automation helps to minimise human error
- Easy auditability
- Significant reduction in time and cost

Efficiency of working with IDM
Through its processes and functionality, identity management positively influences the efficiency of the entire company. Below are typical examples of IDM functionality and capabilities for different types of users.

- Saving competent staff time
- Reduction in the number of requests for IT support
- Increased security of sensitive data
- Audit reports
- Overview of subordinates’ permissions
- Possibility to change / request changes without IT involvement
- Time limitation of permissions, e.g., for freelancers when collaborating on a project
- Quick account setup for new employees/externals
- Reset system passwords without IT involvement
- Request accesses without contacting IT
- Overview of one’s permissions
- Reduced operational time, more time for development and maintenance
- Overview of accounts and permissions
- Quick evidence for audits
- Automation of processes and administration
- Approval processes for granting and revoking permissions
- Managed revocation of accounts and permissions after an employee leaves
- Compliance and management of permissions in accordance with legislation and security standards
- Central audit tool
- Management of temporarily authorized accounts and privileged accounts
IDM initMAX services
- Initial consultation
- Analysis of requirements and needs
- Proposal preparation
- Implementation and testing of the solution
- We offer to take over the existing IDM solution into our service and operation.
- We have extensive experience in implementing and managing diverse IDM solutions
- We have a wide range of IDM professionals
- We are able to efficiently resolve emerging issues and requirements
- Bug fixes for IDM solutions under guaranteed conditions
- Maintenance of documentation
- Manual monitoring of selected critical functions
- Automatic monitoring
- Updates (on request)
- Consultation for customer’s employees in case the system (application) is partially supported by the customer’s own staff
- Minor development – small-scale changes (function additions, appearance changes, etc.)
- Security consultation (risks, threats, proposed solutions)
- Support and process setup
- Methodological consultation
- Mapping the current situation and finding an effective way to address the area
We are happy to share our experience and train you. Visit our training and certification page or attend our free webinars.
You have deployed an identity management or access management tool in your company and you’d like to evaluate the quality of its implementation or get inspiration and recommendations for its further development? Our experts who have experience in real implementations of IAM (Identity & Access Management) solutions are ready to help you in this area.
The result of the audit is a report that describes the quality of the detected solution, summarizes the shortcomings, offers a way to eliminate them and proposes requirements for further development of the solution.
Why initMAX
We are a team of honest professionals who emphasize practical, secure and efficient solutions.
We have more than 15 years of experience in deploying various open-source IDM products, from smallest to largest companies.
We emphasize a precise analysis of your company’s needs and then recommend the best customized product or solution.
In the area of identity management and role management, we build long-term partnerships with our customers. Satisfied references are proof of that.
Identity Management – information
Identity and role management technologies are varied. The initMAX know-how includes tools from Oracle, Microsoft, IBM, Novell and CA as well as open-source solutions for IDM such as OpenIDM, Apache Syncope, midPoint or OpenIAM.
Our work combines two basic approaches to identity management – a methodical approach to IDM and a technical approach to IDM.

In the methodical case, we define procedures for granting, changing, removing identities and permissions, and assign these to people in the organizational chart. We complement the process with forms, registration tables and ways to get reports for security. We appoint the administrators responsible for individual information systems (assets).
Advantages of the methodical approach to IDM:
- Quick to implement
- Can be easily applied to companies with different levels of work organisation
- Soft rules allow to include less standard conditions
Disadvantages of the methodical approach to IDM
- Lots of human elements, susceptibility to intentional and unintentional errors
- Possible time-consuming, depending on workload of system administrators, supervisor and security
- Employee handles the agenda instead of doing the job they were hired for
- Process follows a “smooth line”, relying on the goodwill and loyalty of the employee
- Potential for inconsistencies in information due to different ways in which information is updated
The methodical approach is suitable for such companies:
- Small number of information systems
- Not burdened by regulatory requirements of clients or the law
- The potential impact of information misappropriation is small
- There is low employee turnover
- Examples of clients: used car dealerships, carpentry shops and workshops, cleaning companies
The technical solution puts a specialized system, commonly referred to as an identity manager, at the centre of identity and permission management. This software contains the process and business logic required to automate user introduction to information systems. The processes and procedures here serve as a formal description and aid to identity and permission management.
Advantages of the technical approach to IDM
- The system operates autonomously to a large extent, saving administrators’ work
- There is a central overview of the accounts on the end systems
- Reduces the risk of misuse of information after an employee leaves
- Central management of accounts, permissions and information changes
- It is possible to plan changes for the future
- The solution has the potential to become the basis for further ICT development in the company (management of access, licenses, SSH keys, roles)
Disadvantages of the technical approach to IDM
- The solution is technically more complex the more fragmented the company’s information systems are
- Higher implementation costs
The technical approach is suitable for such companies:
- Medium and larger companies
- Information security is essential
- They work with a larger number of information systems
- A large number of users can be expected
- There are frequent changes in processes and systems
- Examples of clients: educational institutions, public sector, energy and financial institutions

